SSO with Azure AD
Configure SSO using OpenID Connect and Azure AD
OpenID ConnectTo become familiar with OpenID Connect in Budibase, see: OpenID Connect
Configuration
First look for the Microsoft Entra ID service and click it.
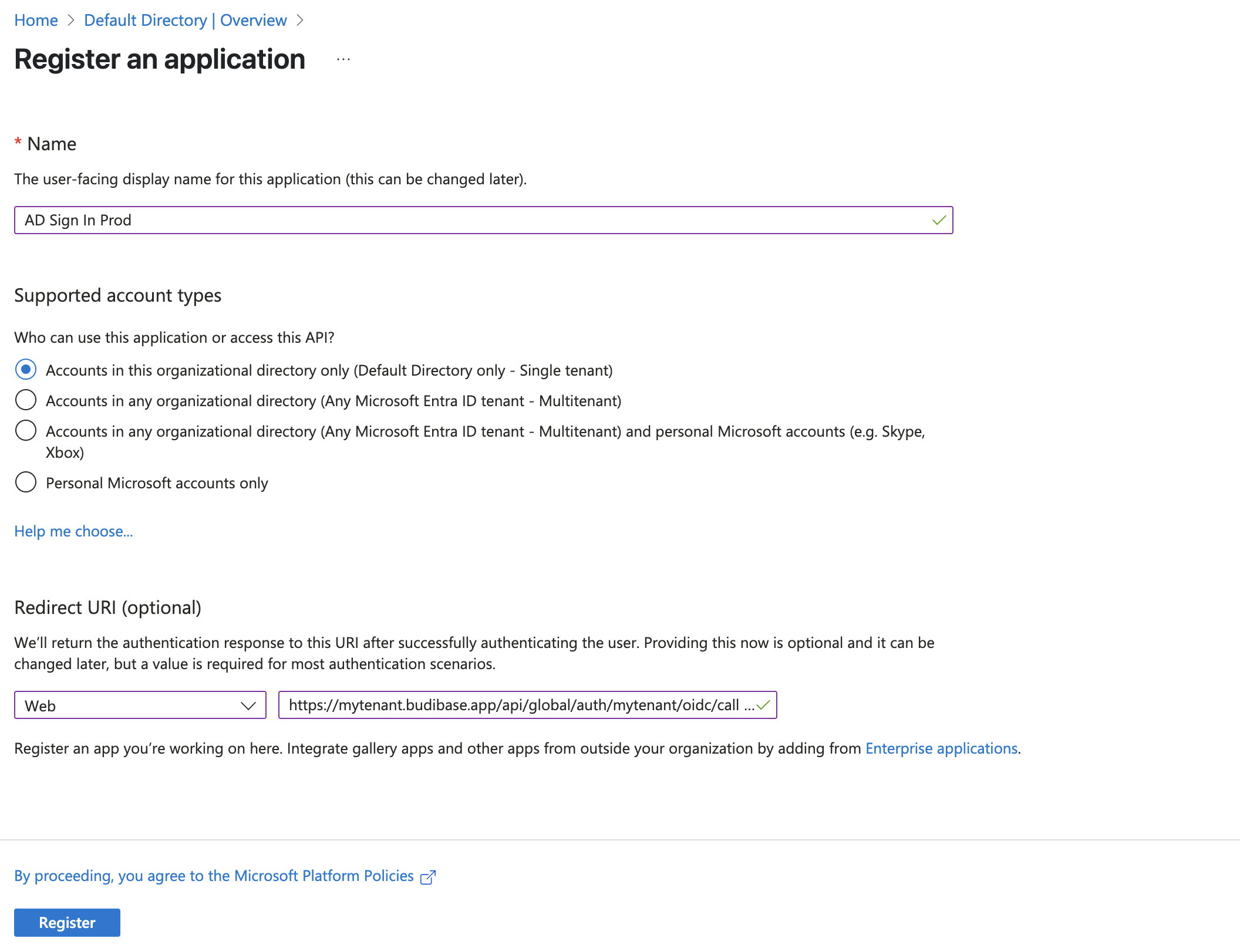
Create the application
Create the Budibase application using a new 'App Registration'
Add the application name
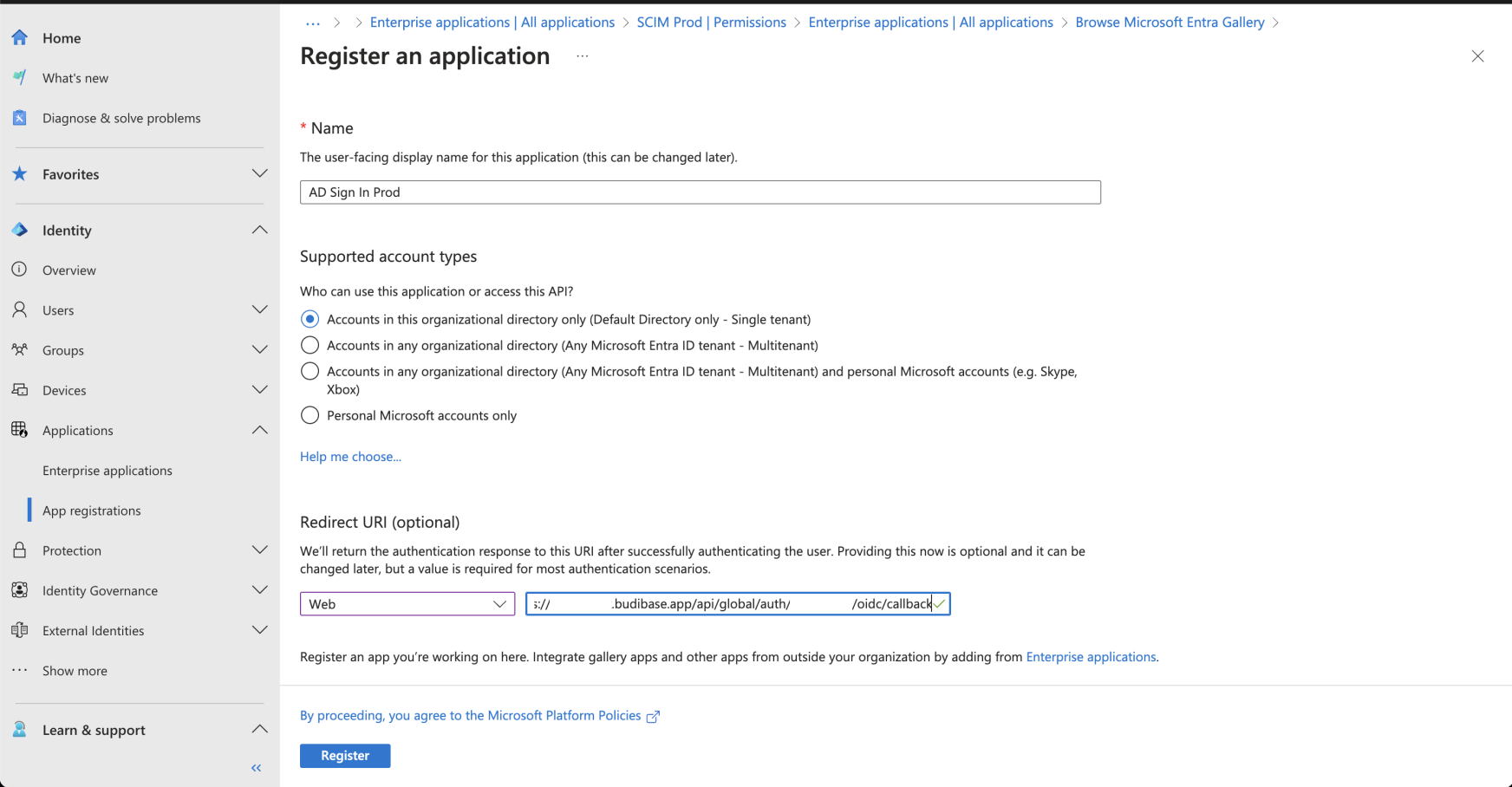
Finding your callback URL
Navigate to Settings -> Auth within Budibase. Scroll down to where it says "OpenID Connect" and find the field labeled Callback URL.
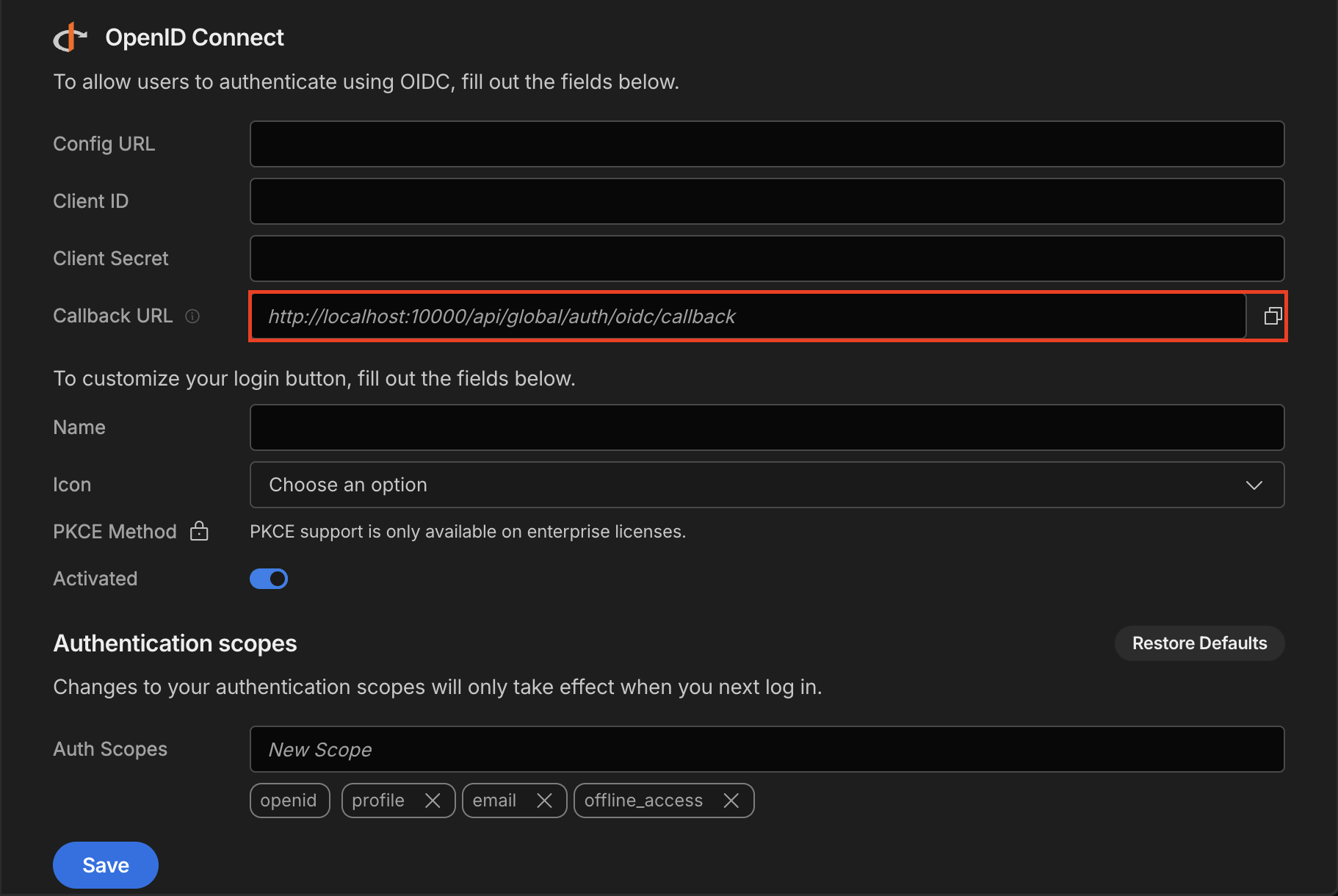
If you are using our cloud service, the URL contained within is exactly what you need.
For self-hosted users, it will likely display http://localhost:10000/api/global/auth/oidc/callback. This will need to be changed depending on how you are hosting it: http[s]://[your-budibase.com]/api/global/auth/oidc/callback. The parts that likely need to be changed are enclosed within square brackets.
Add your callback URL
Switch back to your browser tab for Azure and paste the Callback URL from Budibase into redirect url area.
Find your configuration details
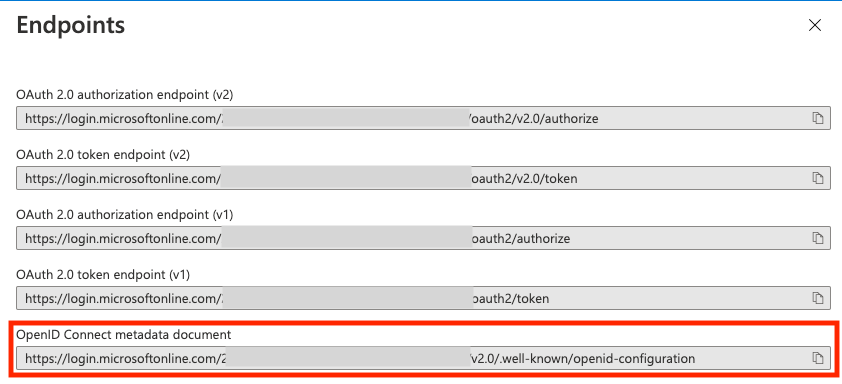
Configuration URL
Visit 'Overview' > 'Endpoints'.
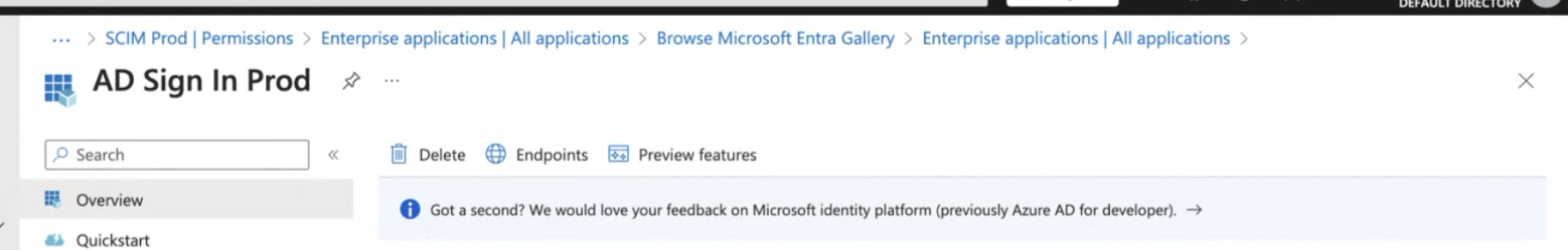
Use the OpenID Connect metadata document field as your Configuration URL in Budibase.
Newer versions of Azure Portal may include a generic OpenID URL like:
https://login.microsoftonline.com/common/v2.0/.well-known/openid-configurationIn that case you will need to manually edit the URL and include the Azure Tenant ID:
https://login.microsoftonline.com/[AZURE_TENANT_ID]/.well-known/openid-configuration
Client ID
Visit 'Overview'
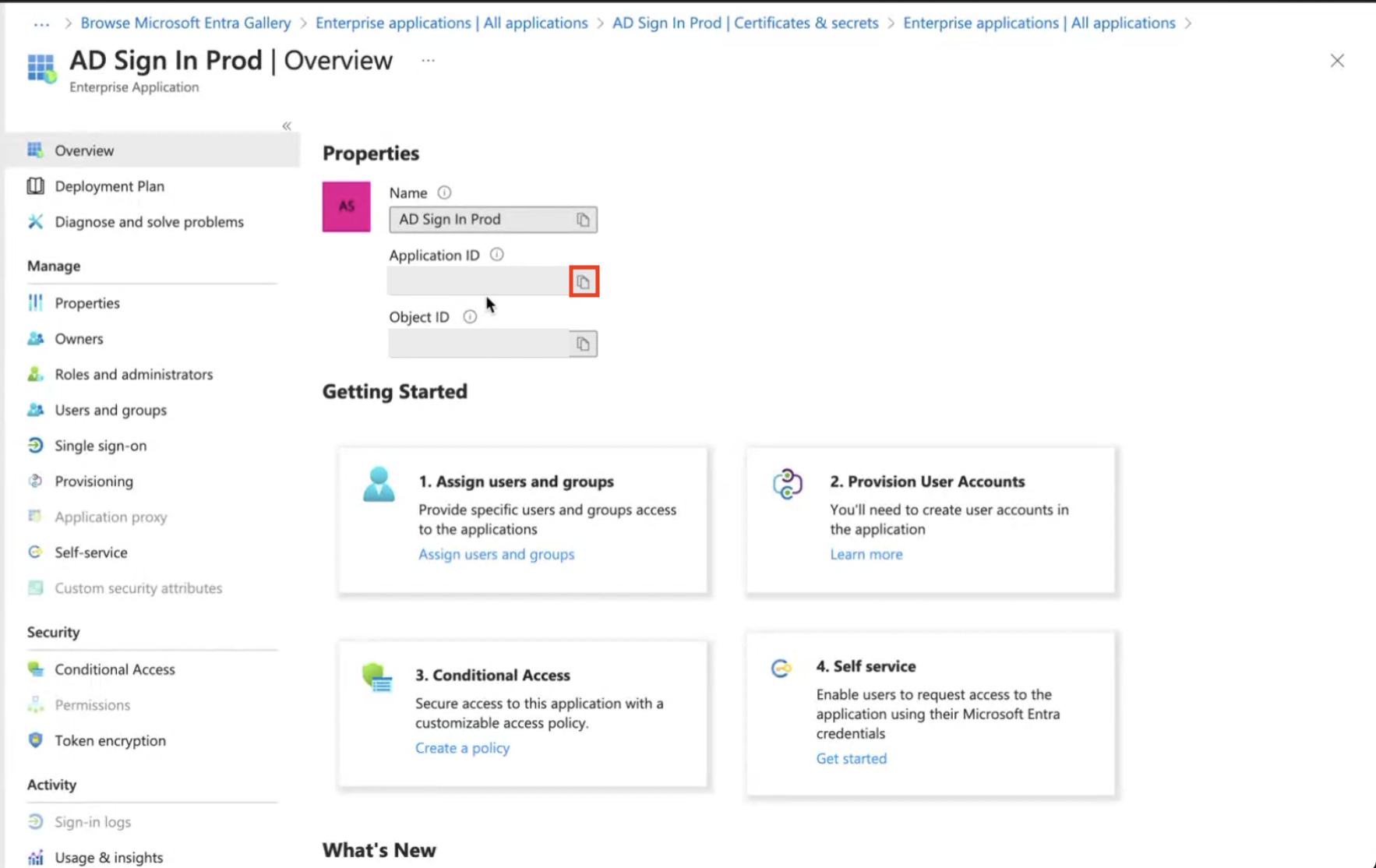
Use the Application (client) ID field as your Client ID in Budibase.
Client Secret
Visit 'Certificates & secrets', click on 'Add client secret', give your secret a description/expiry, and save.
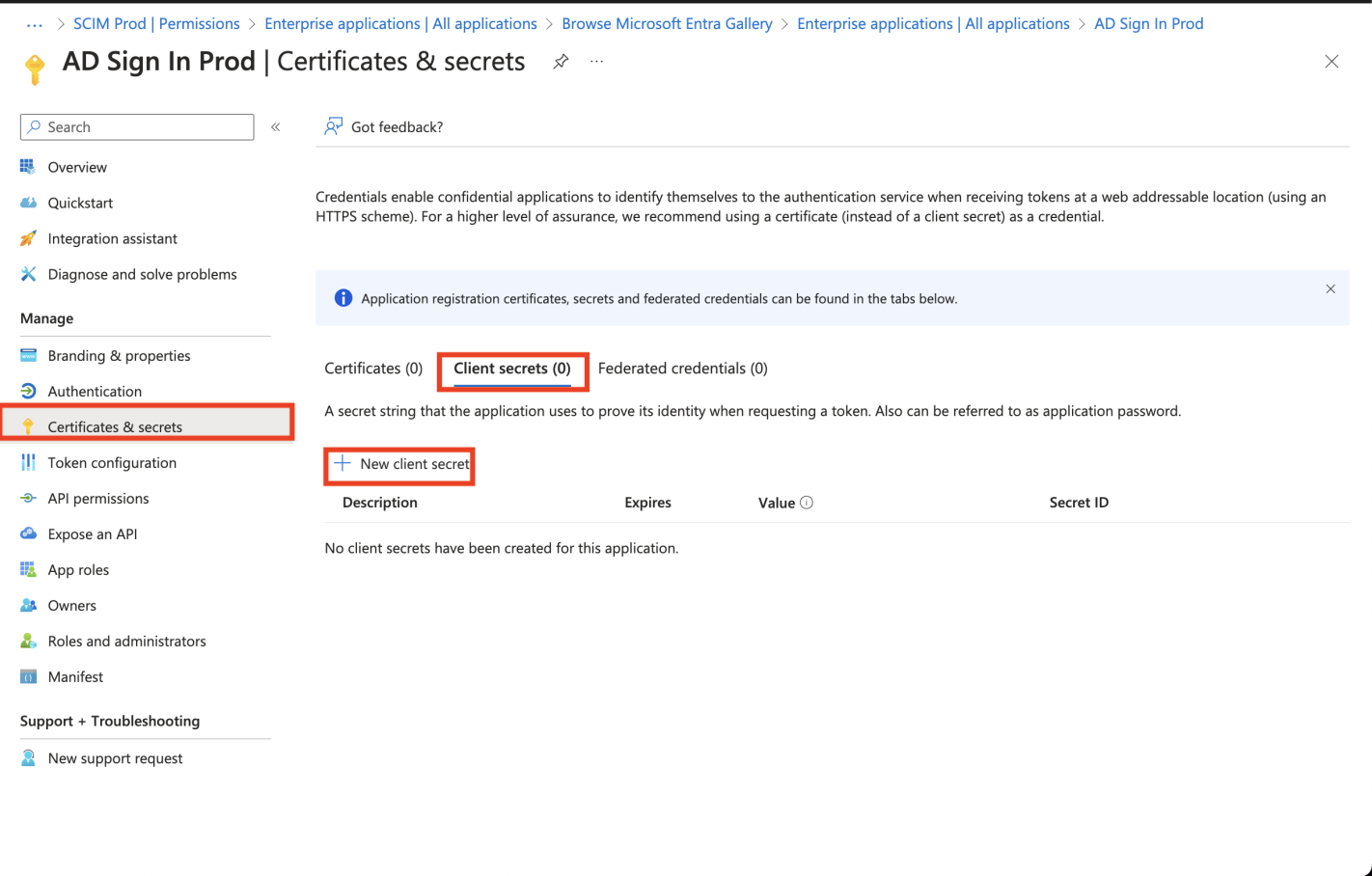
View your newly created secret
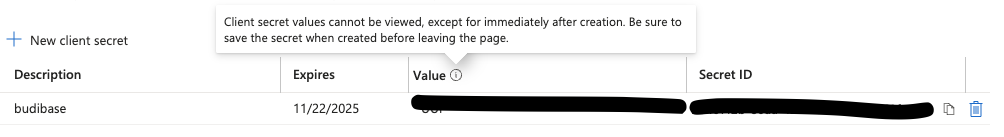
Use the Value field as your Client Secret in Budibase.
Updated 5 months ago